Ethics, Privacy and Patient Rights Commitments of Cancer Image Europe
In the context of the Cancer Image Europe, ensuring compliance with ethical, legal, and privacy standards while enabling responsible data-driven research is paramount. This section will explore the platform’s commitment to data protection, privacy, and patient rights, aligning with key regulations such as the General Data Protection Regulation (GDPR), the European Health Data Space (EHDS), the Data Governance Act (DGA), and the Artificial Intelligence Act (AI Act). To safeguard personal and health data, Cancer Image Europe implements a robust governance framework, combining strict access control, data anonymization or pseudonymization, encryption, and secure processing environments. User authentication, role-based access management, and continuous cybersecurity assessments further enhance data protection. Privacy-preserving technologies, such as access to restricted data and blind distributed processing, allow researchers to analyze data without direct access to personal information.
Privacy and ethical regulations
Cancer Image Europe prioritizes compliance with ethical, legal, and privacy standards while enabling research. Aligned with GDPR, EHDS, DGA, and the AI Act, it ensures data protection through strict access controls, anonymization, encryption, and secure processing. User authentication, role-based access, and privacy-preserving technologies allow data analysis without exposing personal information.
1. Data protection, privacy and compliance with Cancer Image Europe
Cancer Image Europe is primarily focused on harnessing the potential of medical images, clinical data, and advanced tools to enhance cancer care in the era of precision medicine.
However, a critical aspect to consider is the implementation of technical and organizational measures to ensure compliance with key regulatory frameworks, including the General Data Protection Regulation (GDPR), the European Health Data Space (EHDS), the Data Governance Act (DGA), and the Artificial Intelligence Act (AI Act).
The project’s security framework encompasses a robust set of technical measures, both deployed and planned, such as encryption protocols, access management strategies, and disaster recovery planning. These safeguards are designed to protect the confidentiality, integrity, and availability of health data.
From awareness initiatives and data access governance to risk mitigation strategies and compliance with data protection impact assessments, each component is carefully analyzed to highlight the project’s commitment to data security. The intersection of AI and cybersecurity, along with an in-depth focus on Data Protection Impact Assessments, reinforces transparency and ethical data processing.
By systematically addressing risk evaluation, necessity and proportionality assessments, and the identification of mitigating measures, this deliverable serves as a comprehensive guide to Cancer Image Europe’s approach. The project is dedicated to maintaining legal compliance, technological excellence, and organizational resilience, ensuring the responsible and ethical management of health data.
2. Cancer Image Europe GDPR compliance
The General Data Protection Regulation (GDPR) is a comprehensive data protection and privacy framework introduced by the European Union (EU) in 2018. It establishes clear guidelines for the collection, processing, and storage of personal data belonging to EU citizens, granting them greater control over their information. The regulation imposes strict requirements on organizations handling such data, including obtaining clear consent, ensuring the right to access and rectify personal information, and implementing robust security measures to protect data. Non-compliance can result in significant fines, making GDPR a critical legal framework for safeguarding individuals' privacy rights.
Information security is fundamental to protecting these rights. Recognizing its importance, the GDPR enshrines security as a core principle in Article 5, an essential objective, and a binding obligation for data controllers and processors. Under its risk-based approach, controllers must implement appropriate measures in line with the latest technological advancements.
Key Provisions in GDPR

Two of the GDPR recitals are particularly relevant to evaluate the data protection security and required security measures.
The measures include:
- Pseudonymization and encryption of personal data.
- Ensuring ongoing confidentiality, integrity, availability, and resilience of processing systems and services.
- Restoration capabilities to regain access to personal data following a technical or physical incident.
- Regular testing, assessment, and evaluation of security measures.
3. Safeguard measures
In this part, we will describe in detail which technical measures are already in place and those that are planned to be implemented during the development, testing, and application of the services in Cancer Image Europe. This is not an exhaustive list of measures. The listed measures and additional ones need to be continuously reassessed according to the risks and state-of the art technology.
3.1. Technical measures implemented and to be implemented
The three main categories for which specific technical measures should be implemented are: Data Protection, Access and Control and Infrastructure & Monitoring.
Data Protection- To guarantee the confidentiality and privacy of personal data, EUCAIM incorporates robust data protection measures:
-
Pseudonymization: Personal data is replaced with artificial identifiers to prevent direct identification, ensuring that data is handled without compromising individuals' privacy.
-
Encryption: Data is encrypted during storage and transmission, ensuring it remains unreadable to unauthorized parties and safeguarding it from potential data breaches.
-
Archiving & Data Destruction: Data retention policies are strictly followed, ensuring that personal data is securely archived and, when no longer needed, properly destroyed or anonymized in line with GDPR compliance.
Access & Control- Strict access controls are enforced to ensure that only authorized individuals can interact with sensitive data:
-
Access Management: Cancer Image Europe ensures that only personnel with the necessary clearance can access personal data. Permissions are tailored to the individual’s role and responsibilities.
-
User Registration: Users must register through secure identification systems, and access to sensitive data requires approval from the Access Committee. This process is designed to ensure a clear audit trail of all data interactions.
-
Secure Data Transmission: All data transfers are conducted through encrypted channels, ensuring that data is securely transmitted and cannot be intercepted by unauthorized entities.
Infrastructure & Monitoring- The Cancer Image Europe platform maintains a robust infrastructure to protect data and ensure continuous operation:
-
Network Protection: The internal network is secured using advanced tools like Kubernetes and Cilium, ensuring that only authorized services and personnel can access critical data and systems.
-
Backups: Regular backups are performed to mitigate the impact of any technical incidents, ensuring data can be restored promptly if any disruption occurs.
-
Server Maintenance: Regular server maintenance and updates are carried out to protect against vulnerabilities. The platform also employs role-based access to minimize the risk of unauthorized access and ensure the integrity of the system.
The specific details regarding the technical measures undertaken and to be implemented can be found in the EUCAIM project deliverable of WP3 D3.1 [Report on the technical and organizational measures to safeguard the rights and freedoms of data subjects].
3.2. Organizational measures implemented and to be implemented
The organizational measures have been summarized below.
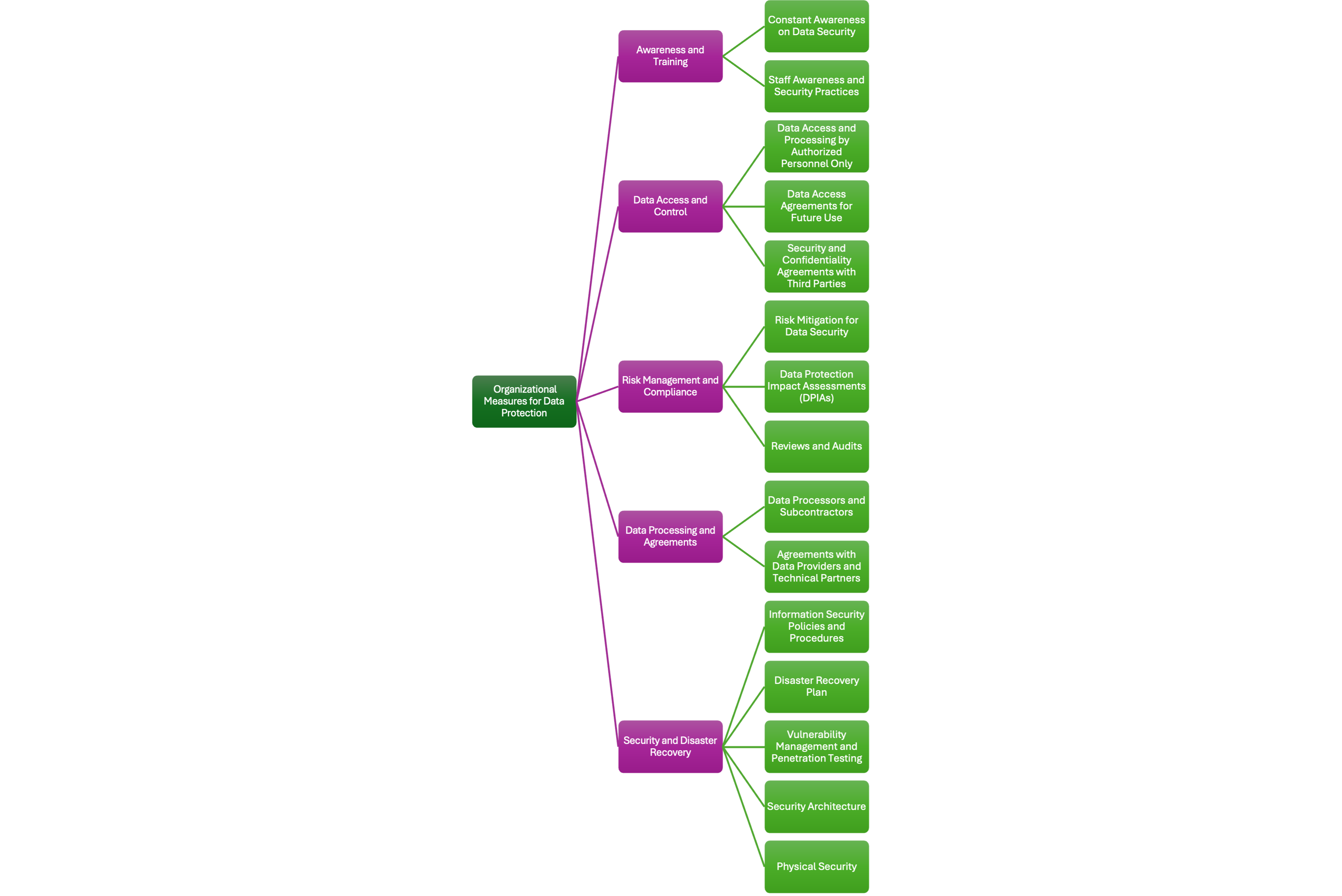
Few considerations can be stated considering the importance of working in a controlled and secure environment.
Constant Awareness on Data Security
Raising awareness on data security is achieved by appointing responsible individuals and providing them with the necessary resources and authority. Coordination between key personnel ensures that monitoring and protection of access to physical spaces and equipment are in place. Regular system checks and security updates help maintain appropriate measures.
Security and Confidentiality Agreements with Third Parties
Security and confidentiality agreements with third-party operators are essential. These operators, such as those providing hardware maintenance, are required to sign necessary contracts and undergo appropriate supervision by data centers. Each data center follows its own policy regarding third-party agreements.
Data Access and Processing by Authorized Personnel Only
Strict access controls are implemented to ensure that only authorized individuals can access or process data. Authentication methods are employed, and user access rights are reviewed and revoked when no longer authorized. Three access levels are defined: anonymous, registered users, and users with specific data access permissions.
Risk Mitigation for Data Security
Cancer Image Europe ensures that users adopt both technical and organizational measures to protect data. Legal instruments such as Data Transfer Agreements (DTA) and Data Access Agreements (DAA) are utilized to enforce these measures. These agreements define the roles and responsibilities related to data protection and transfer.
Data Processors and Subcontractors
Data Processing Agreements are signed with each third party handling personal data. These agreements ensure that processors and subcontractors meet GDPR requirements. Cancer Image Europe uses a rigorous due diligence procedure to select processors, ensuring compliance with data protection standards.
Staff Awareness and Security Practices
Human error is a common cause of security breaches. Staff training programs help identify threats such as phishing and malware. Regular awareness sessions and updates ensure that everyone involved understands the security measures in place and the potential consequences of non-compliance.
Data Protection Impact Assessments (DPIAs)
DPIAs are conducted for high-risk data processing activities, particularly when processing special categories of data, such as health or biometric data. These assessments help identify and mitigate potential risks to data subject rights and freedoms.
Agreements with Data Providers and Technical Partners
Formal agreements with data providers and technical partners outline responsibilities and obligations for data protection. These agreements help ensure that all parties comply with security requirements and data handling protocols.
Data Access Agreements for Future Use
A Data Access Agreement template will be drafted for future data usage. This template ensures that data usage is restricted to the scope approved by the Data Access Committee and data providers.
Information Security Policies and Procedures
The platform adopts policies and procedures covering various security aspects, such as remote access and asset management, ensuring comprehensive protection of data and systems.
Disaster Recovery Plan
A Disaster Recovery Plan is being developed to outline actions required to recover from major incidents. The plan focuses on minimizing service disruption and ensuring the availability of data and services in case of emergencies.
Reviews and Audits
Regular reviews and audits assess the effectiveness of the implemented security measures. The platform undergoes routine security scanning, penetration testing, and compliance checks to ensure continuous improvement.
Vulnerability Management and Penetration Testing
Continuous monitoring and vulnerability management are implemented to identify and fix security issues in the platform. Periodic penetration tests assess whether the platform is adequately protected against potential threats.
Security Architecture
Cancer Image Europe follows a hybrid federated-centralized model that integrates research infrastructures and repositories. This model ensures secure access to data while providing centralized governance for data processing and storage.
Physical Security
Physical security measures are put in place to protect the data infrastructure. These include fire detection systems, biometric access controls, surveillance cameras, and secure card access systems. Backup facilities are distributed across different locations to mitigate risks related to data loss.
4. Guidelines and references
-
EDPB, “Guidelines 4/2019 on Article 25 Data Protection by Design and by Default” Version 2.0. Adopted on 20 October 2020, EDBP Guidelines
-
Deliverable D3.1 “[Report on the technical and organizational measures to safeguard the rights and freedoms of data subjects]”

